Every organization, no matter the size, has federal, state, or local laws and regulations that they need to meet. The burden is even greater in enterprise organizations, which often have many office and data warehouse locations. That means they have even more compliance regulations to adhere to. Failing to adhere to laws can be costly. Noncompliance not only results in costly fines but also can damage a company’s reputation and put employees and their data at risk.
Compliance is an essential part of any company’s operational strategy. But let’s face it: it can also be a huge pain and point of anxiety for IT and security leaders because of its complexity. But, there’s good news. With the right strategy and tools, keeping your business in compliance doesn’t have to be a burden.
In this ebook, we’ll show you what the compliance ecosystem looks like today so you can begin building an enterprise-wide compliance culture. We’ll also cover the most common compliance standards you should know about. This should help inform or improve your organization’s compliance management program. Finally, we’ll break down some compliance worst-case scenarios—and how to avoid them. There’s a lot to cover, so let’s get started with our first topic: what exactly is compliance and why does it cause such a headache?
Read on to learn:
The importance of workplace compliance
Every time you sign a HIPAA privacy form at your doctor’s office, get locked out for mistyping your password too many times, or receive a notification about updated privacy policies online, you’re experiencing something to do with compliance. Businesses are required to meet specific mandates regarding data security, privacy, and workplace security.
A common misconception about compliance is that obtaining compliance certifications is all you need to worry about. Certifications provide peace of mind, but maintaining business compliance is not a one-time, annual activity. Keeping track of international, federal, and state laws governing an organization is an ever-changing process. Corporate policies and procedures need to be continuously evaluated and updated. Especially with the dreaded audit.
In recent years, regions, countries, and states have implemented multiple mandates and policies to protect individuals’ privacy and give people more control over their personal information. These laws may require that companies put protocols in place to ensure that sensitive data stays secure. Putting together formal plans and hiring dedicated professionals to enact these policies is part of compliance management. Though compliance touches many parts of a company’s operations, more often than not, many of these duties fall within the jurisdiction of IT teams.


What’s an audit?
A compliance audit is a comprehensive review of an organization’s adherence to regulatory guidelines, often conducted by independent third parties. Audit reports evaluate the strength and thoroughness of compliance preparations, security policies, user access controls, and risk management procedures. Compliance auditors will generally ask members of the C-suite and IT administrators a series of pointed questions that may include what users were added and when, who has left the company, whether user IDs have been revoked, what visitors were on-site and when, and which IT administrators have access to critical systems.
The end-result of a failed audit can mean serious fines and business disruption for your company. In 2021, the average cost of non-compliance came in at a staggering $14.82 million. In fact, the average cost of non-compliance has risen more than 45% over the past ten years. But compliance isn’t only important to avoid potentially business-ending fines. It’s also essential to manage risk, protect your employees and their data, maintain your brand’s reputation, and ultimately, secure the future of your business.

The hidden costs of non-compliance
An organization loses an average of $5.87 Million in revenue due to a single non-compliance event. But the financial impact goes far beyond just revenue—it’s vastly more expensive to your company’s bottom line. To understand the true cost of a non-compliance event, you have to consider some of the hidden costs.
The total cost of non-compliance averages $14.82 Million and comes from:
- Fines, penalties, and fees
- Business disruption
- Revenue loss
- Productivity loss
- Loss of assets
- Reputation damage
How to create a compliance culture in the workplace
Everyone in a workplace plays a role in keeping your organization compliant. After all, compliance impacts every aspect of your business. Moreover, everyone in the workplace has access to sensitive data and information. For large enterprise organizations, compliance doesn’t only fall on the IT and security teams who manage the compliance programs. If employees aren’t educated on how to keep company data safe, they might be a security risk to your organization.
Here are the main roles, policies, and tools your enterprise needs to create a compliance culture.
Your compliance management tiger team
With the rise of compliance management, companies are creating new titles and responsibilities. A compliance team can be one person or an entire department. No matter how many people you have on staff, your compliance team should have five areas of responsibility: identification, prevention, monitoring and detection, resolution, and advisory. Here are a few roles you might want in your compliance management tiger team:
- Compliance manager. A compliance manager stays up-to-date on relevant laws and regulations and ensures that the company adheres to them to minimize financial and legal risk.
- Data protection officer. A data protection officer is responsible for creating and managing a company’s data protection strategy and implementation.
- Risk management officer. A risk management officer identifies vulnerabilities and risks that an organization faces and advises on how to avoid or address them.

“BuzzFeed takes our employees’, freelancers’, and partners’ privacy extremely seriously. We have two full-time employees as well as a formal guidance council that run our day-to-day data transaction activities and cyclical reporting programs. In addition, we have in-house Legal Counsel whose sole focus is employee and data privacy.”
JULIA GOLDBERG
SVP of Global Real Estate, Office Services, and Security at BuzzFeed
Two internal policies to have in place to stay compliant
With your team in place, it’s time to create policies to ensure that your organization stays compliant and avoids costly security risks. Here are two policies to have in place to maintain your compliance culture company-wide:
- Conduct internal audits to get ahead of any vulnerabilities. An internal audit is a chance to look inward at the processes and programs in a company to see how you’re doing. Think of an audit the way you’d think of running a diagnostics program on your computer. You don’t know for sure if something is wrong, but if there is, you want to know about it so you can fix it before it becomes a problem. Create a policy for your compliance tiger team to conduct a regular, annual internal audit to spot vulnerabilities before they are a problem and create a plan to address them.
- Train your employees to avoid costly security risks. Engaging employees on compliance topics is no easy task. However, it’s important to socialize the message that compliance is everybody’s responsibility. Create an easy and digestible way for employees to understand the policies and code of conduct that they must adhere to—and make sure you customize it by location. You’ll want to train folks regularly, make the information readily accessible, and monitor and measure your efforts.
What do your employees need to do?
Every single person in your company handles personal information in some way. Therefore it’s every employee’s responsibility to maintain compliance. Here are a few examples of different teams beyond IT handling data that needs to stay secure:
Finance:
Personal addresses, credit card numbers, bank account numbers
HR:
Social security numbers, names and addresses, phone numbers, self-identification, immigration, and other demographic information
Marketing:
Email addresses, cookies, browsing histories, click-tracking, mailing preferences, social media activity, and in some cases, names and images
Operations:
Customer names, client contacts, purchasing histories, visitor logs
Enlist the help of an enterprise-grade workplace platform
Workplace technology is another important piece of establishing a compliance culture on-site. Many organizations feel pressure to build sustainable infrastructure and processes to ensure compliance.
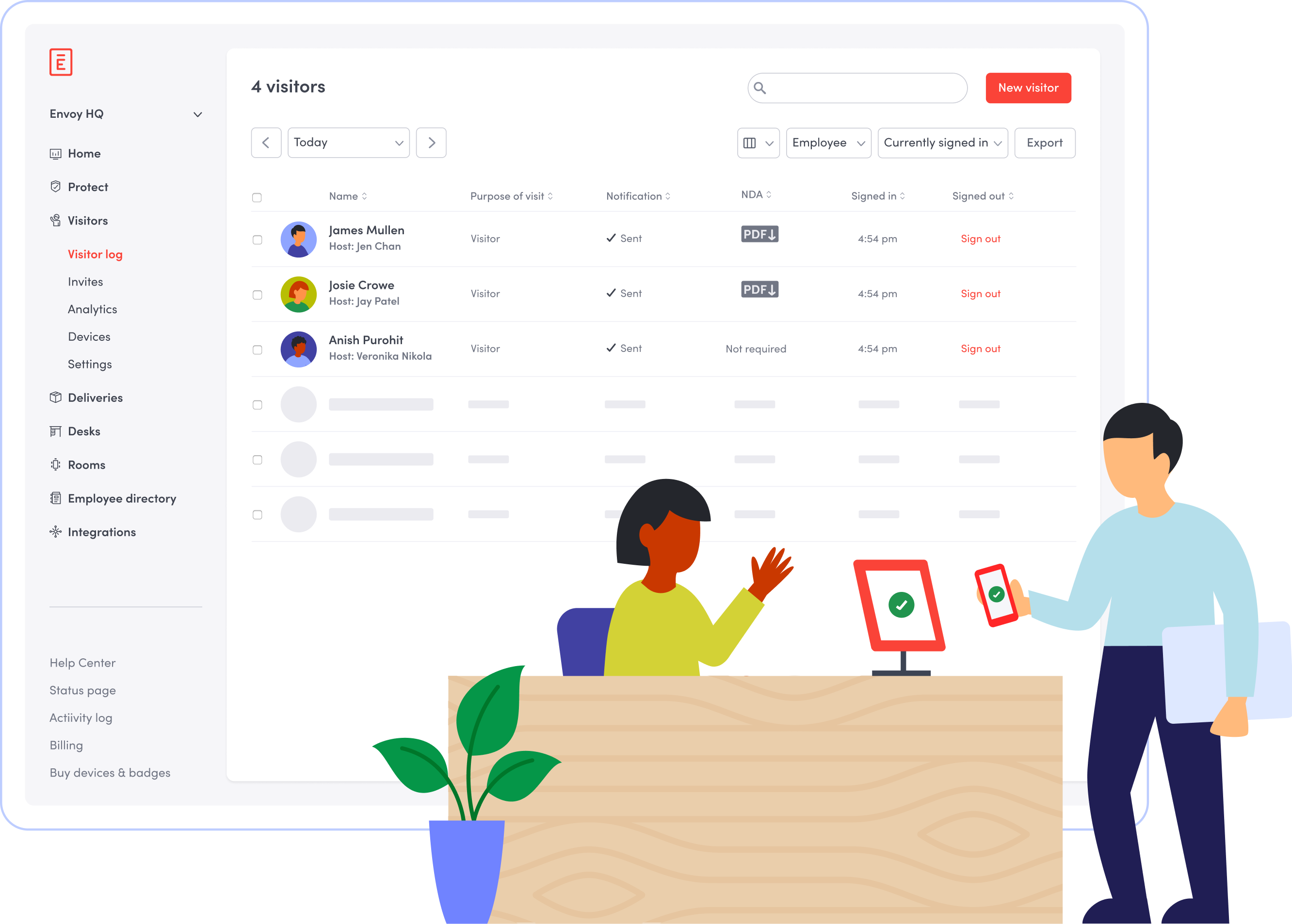
One part of a company’s operational infrastructure includes managing who comes in and out of your workplace on a daily basis—this includes visitor management. Going digital with your visitor management will help you maintain compliance. You’ll benefit from:
- Cloud-based data storage: Flag individuals who should not be allowed into designated areas through advanced blocklists, ID checks, and cross-checks with third-party watch lists
- Secure data collection and anonymization: Streamline compliance with data privacy laws by storing your visitor’s personal information in a centralized, secure location
When the COVID-19 pandemic hit in 2020, the Centers for Disease Control and Prevention (CDC) and the Occupational Safety and Health Administration (OSHA) issued mandatory guidelines for businesses on how to prevent and reduce transmission of COVID-19 at the workplace. As a reaction to this, companies needed a way to securely store private personal information related to employee health. To manage this, many enterprises invested in a workplace platform that allows them to:
- Verify vaccination status or COVID test results,
- Conduct daily health checks,
- Keep track of which employees are on-site and when,
- All while protecting personally identifiable information
Mitigating compliance risks without disrupting your workplace experience might seem daunting. With the right technology, you don’t have to choose between ironclad security compliance and an amazing workplace experience.

“Envoy is a one-stop shop for us in terms of gathering data, providing permissions, and sending approvals—all within our SOC and GDPR requirements. As the pandemic progressed, we had less in-person power to run these systems. Workplace platforms like Envoy are invaluable ‘silent’ partners in our ability to keep our offices up and running, which directly enables us to continue production and maintain a level of culture that would have otherwise been lost.”
JULIA GOLDBERG
SVP of Global Real Estate, Office Services, and Security at BuzzFeed
The rise of cloud-based software—and its implications on compliance and security
Today, many business operations run on cloud-based workplace technology. Think visitor management, document storage, and remote communication and collaboration tools. While moving to the cloud has many benefits, maintaining cloud-based processes and systems can also pose compliance-specific operational risks.
Why does this matter to business compliance? The answer is simple: data storage. How your organization stores data can be a huge challenge for your business. You must thoroughly understand and openly communicate where company data is located. You must also have procedures in place to effectively protect this data. Falling short in any of these areas can ring alarm bells during an audit. Worse, it could compromise the data of your customers and employees.
Take, for example, when the consulting firm Cambridge Analytica gained unauthorized access to up to 87 million Facebook users’ data. This preventable misuse of data resulted in the California Consumer Privacy Act (CCPA), which enhances privacy rights and consumer protection for California residents.
Complying with various local and international data privacy compliance efforts, such as the CCPA, starts with understanding where your business stores its data. Because compliance mandates can differ from location to location, it’s especially important for enterprise organizations to stay on top of their data storage. Read on to learn some of the most common compliance standards your business should know about.

5 common compliance standards enterprises should know about
Feeling overwhelmed? You’re not the only one. The acronyms alone are confusing. In this chapter, we spell out the five most common compliance standards designed to protect personal information data. We’ll also share tips for how you can use this information to inform or improve your organization’s compliance policies.
1. General Data Protection Regulation (GDPR)
The GDPR is a personal data privacy regulation from the European Union (EU), created to protect the privacy of European citizens. The EU passed it in response to corporate abuses in sales and disclosure of user information for marketing and research. If your company offers goods or services to EU citizens, then the GDPR applies to you: any entities that process the personal data of EU citizens need to comply.
This can be as simple as having a customer, client, or vendor from the EU visit your workplace. In order to keep your visitor management process GDPR compliant, you’ll want to consider:
- Getting explicit consent from visitors. Allow visitors to opt-out of data storage when they sign in. If a visitor does not consent to data collection, give them another way to sign in.
- Disclosing data usage. The GDPR requires that you disclose how individuals’ data will be used. With digital visitor management, companies can display custom data use policies directly within the sign-in flow.
2. Service Organization Controls (SOC 1 & SOC 2)
SOC is a suite of reports established by the American Institute of Certified Public Accountants (AICPA) relating to the cybersecurity of an organization. SOC certified organizations undergo regular audits involving the controls over information technology and related processes, policies, and operational procedures. SOC 1 and SOC 2 are the most common.
- SOC 1. SOC 1 compliance is relevant to business services that process private individual data related to financial statements, such as payroll management (for a company’s employees and customers).
- SOC 2. SOC 2 specifically focuses on data security compliance around five trust service principles: security, availability, processing integrity, confidentiality, and privacy. Obtaining SOC 2 certification means that you need oversight into who, what, when, where, and how people had access to your facilities and technology. That’s where access control and visitor management come into play.
Hot tip: Access control and visitor management systems can help you meet the security goals of your SOC 2 certification. These two, when integrated together, provide an auditable, real-time tracking of both employee and visitor data. Here are a few features to look out for:

- Visitor and employee logs. Maintain secure, digital visitor and employee logs that capture data about whois on-site, when they check in and out, and what parts of the building they accessed.
- Visitor identification verification. Use photo capture, ID checks, and blocklists to verify your visitor’s identity and approve or deny access tothose who are not permitted
- Visitor and employee badges. Create badges that identify employees and visitors and properly give them access to the appropriate areas of your workplace.
3. International Traffic in Arms Regulations (ITAR)
ITAR is mainly relevant to the manufacturing industry and is designed to help ensure that defense-related technology does not get into the wrong hands. If your company deals with defense-related services, products, or technical data, you are most likely familiar with ITAR compliance.
Record-keeping, visitor scanning, and tracking are key elements in ITAR compliance. This is where your secure visitor management system can help you maintain an ITAR-compliant visitor logbook. Your visitor management system should keep detailed reports to assist with audits, security protocols, and on-premises visitor controls.
Hot tip: An ITAR-compliant visitor management system can help organizations meet ITAR’s regulations around verifying citizenship and visitor access by:
- Verifying visitor identity by capturing photos, checking ID’s, pre-registering visitors; then denying access to those who are not permitted
- Creating different sign-in flows based on country of origin or citizenship
- Capturing and storing necessary information, like requiring the visitor choose their country of origin or citizenship
- Requiring a host, with the option to display the host’s name on the visitor badge
- Customizing visitor badges based on authorization levels
4. Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is US legislation that requires that individuals’ protected health information (PHI) be kept private and secure by any “covered health entity.” This includes health providers, health plans, hospitals, insurers, and health clearinghouses that process health information, as well as any business associates that assist these organizations with their work. Two of the main components of HIPAA are the Privacy Rule and the Security Rule.
- The HIPAA Privacy Rule requires that protected health information be kept private and only disclosed when necessary to deliver care or to facilitate payment for services.
- The HIPAA Security Rule requires that health information be stored and transmitted securely. This is especially important with the shift to electronic health records, digital platforms, and the expansion of telehealth.
For a healthcare organization to be HIPAA compliant, administrative, physical, and technical safeguards need to be in place to protect electronic protected health information. This, of course, includes keeping track of who visits the workplace, including employees, facility operations staff, outside vendors, pharmaceutical salespeople, and healthcare contractors.
5. International Organization for Standardization 27001 (ISO 27001)
ISO 27001 is the leading international standard focused on information security. These standards are concerned with information management and security systems. They cover information relating to employees, finances, and intellectual property, among others.
ISO 27001 provides a framework to help organizations, of any size or any industry, to protect their information in a systematic and cost-effective way, with specific requirements related to the organization. One of the specific requirements relates to workplace access control and physical security. In order to maintain ISO 27001 compliance, organizations need to create an access control policy.
Hot tip: ISO 27001 specifies the need to establish, document and review the access control policy periodically–meaning that a documented policy is mandatory! Here are seven areas to include to structure your policy effectively:
- Introduction
- Policy statement
- Roles and responsibilities
- Information/systems access
- User registration/de-registration
- Secure log-on requirements
- Physical access controls
4. Some compliance worst-case scenarios—and how to avoid them
Compliance failures that can threaten organizations aren’t just the ones that make the news headlines—and they happen more often than you might think. Here are some of the more commonplace ways that compliance can go awry to keep an eye out for in your business.
During office moves
An office manager or front desk team might unintentionally compromise your visitor management compliance. A physical move (even within the same building) leaves an opportunity for important documents to go missing if you’re using pen and paper visitor logs and NDAs. Often, the loss of visitor logs isn’t discovered until it’s too late, and an external audit reveals missing information that can’t be accounted for.

In natural disasters
Every region has unique environmental and weather concerns, including winter snowstorms, tornadoes, hurricanes, and earthquakes. Compliance doesn’t only apply to a workplace setting. The physical security of your data centers that process and store any company, employee, customer, and visitor data is of equal importance to the workplace.
As much as you plan for and consider how a natural weather event could impact your workplace, you need to also look into and understand the environment in which your data centers operate. What would happen if a natural disaster, like a flood, occurred? What measures are in place for that data center to ensure reliability? A data center is not only responsible for overseeing the physical security of these facilities and controlling who has access, but mitigating extraordinary events like extreme weather.
Due to human error
This includes but is not limited to spilling water on papers, misplacing or recycling them, and not disposing of sensitive materials in the proper way. A well-meaning employee could leave the front desk unattended, and if there are paper and pen logbooks there, anyone waiting in the reception could access or even take that information.

In third-party audits
A dramatic event doesn’t necessarily have to happen for you to revisit and have to make available any visitor or employee logs, documents, NDAs, and other sensitive materials. Part of your company’s commitment to information security standards is being prepared for third-party audits at any time. But there doesn’t have to be unpleasant surprises when it comes to audits. Instead of being wary of what they might find, think of these external audits as an opportunity to put your compliance policies and procedures to the test. Do the work now to avoid any unexpected issues in the future.