Workplaces are evolving and security teams have a lot of work to do to keep up. More companies are adopting hybrid work, a flexible working model that allows employees to work remotely for part of the week. With a distributed workforce, the threat landscape is broader and security must expand to protect it.The pandemic has proven that teams are already stretched thin. Security leaders need their teams to concentrate on projects that’ll have the most impact on securing the hybrid work environment. Let’s take a look at what they can do to prioritize security improvements.
Perform a security assessment
We won’t spend too much time on this since we covered how to perform a security assessment for hybrid work in another post. An assessment is a structured method of identifying threats to your company’s security. It’ll help you analyze your security posture across your entire work landscape. This process will reveal catastrophic gaps in your programs and pinpoint exactly where your team needs to focus its attention.
Start prioritizing work based on risk level
Now that you know where you need to improve your security programs, it’s time to prioritize your team’s work. The easiest way to do this is by creating a list of security threats to your company. Go through the threats one by one and assign each a risk score. To ensure standardization, use a scoring matrix. In the example below, we used a scoring matrix from our security assessment toolkit to assign a risk level to each threat. As you can see, the matrix we used has four levels of risks: intolerable, high, critical, and moderate.
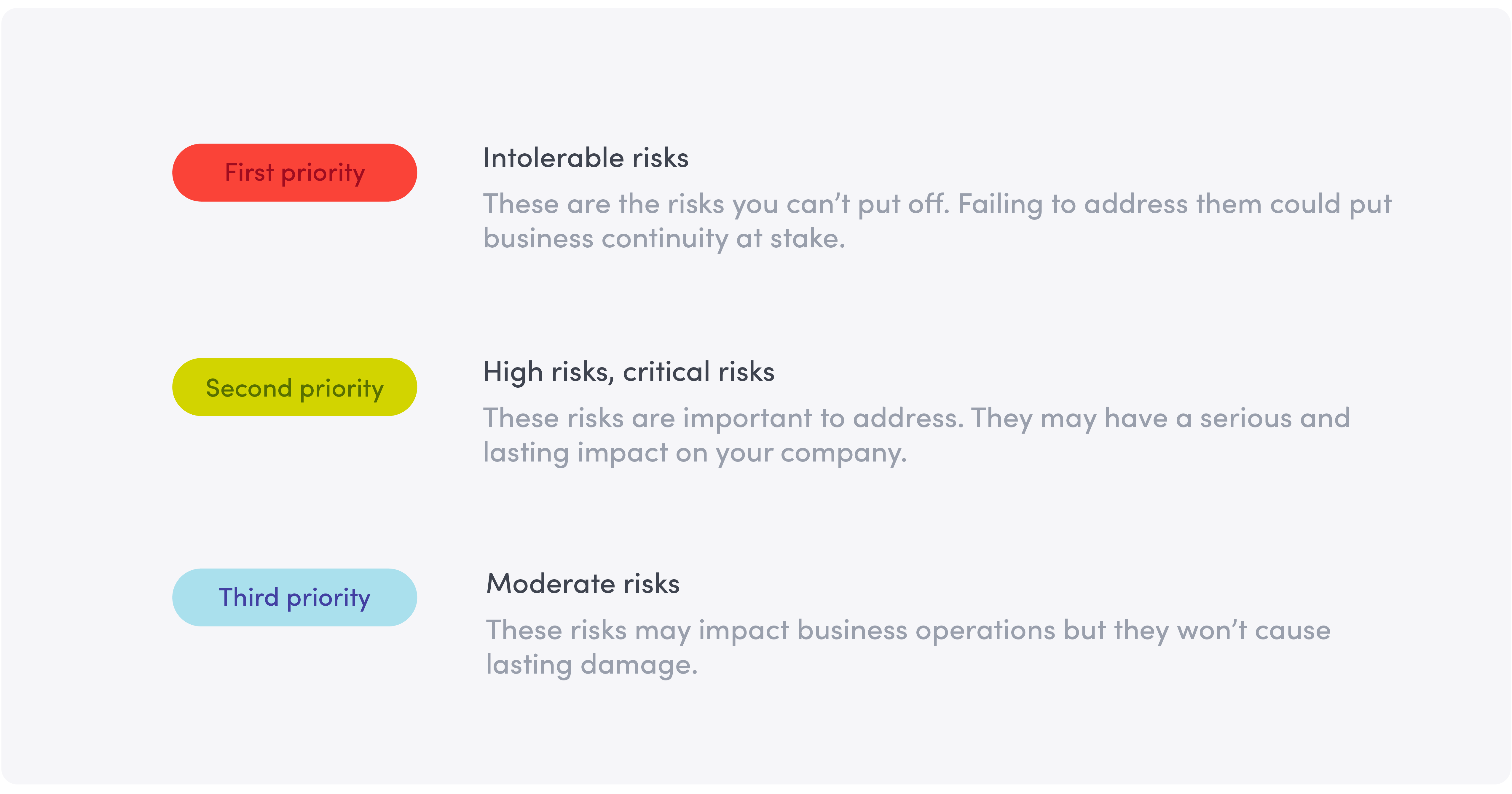
When you’re done assigning risk levels, bucket the threats by priority. In our example, risks labeled as “intolerable” are first priority and must be addressed right away. “High risks” and “critical risks” are the second priority—important but less urgent. Finally, “moderate risks” are the third priority and should be addressed after the higher priority risks.
Prioritizing your work is a simple, yet often overlooked step to working more efficiently—especially when your time and resources are limited. It’s also a great way to give your team a visual of the work they need to do and where they should direct their attention first.
Prioritizing your priorities
One of the realities of adopting a new model of work is that it has big implications on every aspect of the business, security included. You could sort your priorities to find that there’s a lot of high-priority work to do. This may feel like you’re back at square one—too much to do and no way of knowing where to start. If so, do another sweep through your priority lists to force rank your work. Here are three categories to consider to know how to create your high-priority list:
- CostPrioritize based on cost-effectiveness. Some robust solutions eliminate risk entirely but come at the expense of other improvements. Consider the tasks with lower-cost solutions that lower the risk of a threat to an “acceptable” level. By whittling down the risk, your team can turn its attention to other high-priority work.
- Ease of implementationPrioritize based on the amount of work a project requires of your team. Consider both time and ease of implementation. Are there threats on your high-priority list that you can thwart with relatively low effort? If so, you might have your team knock them off the list first. This can give them a sense of progress, which is important when there’s a lot of work ahead of them to tackle.
- Opportunity to scalePrioritize based on projects that scale. Look for opportunities to improve efficiency by scaling solutions across multiple offices. Working on high-risk, scalable projects first will ensure your team prioritizes the work that will have the biggest impact on your security posture. For example, in a hybrid work model, office lobbies have a lot more foot traffic coming and going. Say your team is concerned about trespassers using stolen employee IDs to enter the workplace and gaining access to sensitive information. To prevent manage who’s on-site, you might implement a visitor management system. If your company has multiple workplaces that need this solution, you can scale it across each location in a single, streamlined effort.
By using these additional criteria, you’ll be able to add more structure to your team’s work. You should get input from your team to decide what work is cost-effective, easy to implement, and scalable. You may be able to identify high-priority projects that fall under all three categories!
—
If a hybrid work model is new to your company, you probably have a lot of work to do to close security gaps that come with this workplace evolution. You may need to establish critical systems or processes to guard against new threats. Prioritizing this work will keep your team aligned and focused on the most critical initiatives.
Want to learn more? Download our ebook, An executive framework for scaling hybrid work security. We’ll show you how to assess and prioritize improvements across your organization to keep your company safe.
Read more
Workplace security is critical to the future of your business. Learn why it matters, what threats to watch for, and how to strengthen your workplace security plan.
Searching for a visitor management solution? Learn what to look out for and how to choose the best tech for your team.
Managing your space well doesn’t have to be difficult. But if you want to be successful, you need the right approach.
A well-run workplace can set your team up for success. Learn why workplace management matters and how to do it right.
With more folks sending personal packages to the workplace, having a sound mailroom management system in place is key.








