Hybrid work is in high demand. More than half of employees want to move away from the traditional five-day office workweek. With the COVID-19 vaccine expected to roll out to the general public in spring in the US, companies need to work quickly to secure a flexible work environment. If you’re a security leader, you have an opportunity—and the executive buy-in—to make improvements to your programs at scale. Conducting a security assessment will give you a big-picture view of your company’s preparedness for hybrid work. It’ll reveal security gaps and help you prioritize improvements to mitigate risks. Armed with a framework, you can perform an assessment in three straightforward steps.
Step 1: Identify stakeholders and involve them early
Working closely with cross-functional partners will help you get important points of view before, during, and after the assessment. These folks will ensure you have access to the people and technical resources you need for the assessment.You may need to include people in:
- Compliance
- Workplace
- Facilities
- HR
- IT
- Executive leadership
Consider hosting a kickoff meeting with stakeholders before you start the security assessment. Get people in the same room (or on the same video call) to chat about roles, responsibilities, and timelines. Aim to paint a clear picture of the goals you want to accomplish and how stakeholders can help.
Step 2: Create a scoring system
A security assessment requires you to evaluate your security across pillars and workplaces. To do that, you need to develop a scoring system. Let’s take a look at what you need to do to create one.
Part 1 - Identify threats
Create a list of security threats that fall under each pillar, starting with physical security. Then move on to people security, data security, and so on. Make sure each list includes threats specific to hybrid work. For example, your list for the data security pillar may look like this:Data security threats
- Phishing scam
- Ransomware attack
- Malware/virus
- Unauthorized disclosure of customer data
- Unauthorized disclosure of employee data
- DDoS attack
Answering the question, “what’s the worst that can happen under this pillar?” will help you identify the most significant threats. Don’t forget to get stakeholder feedback, so other opinions are represented.
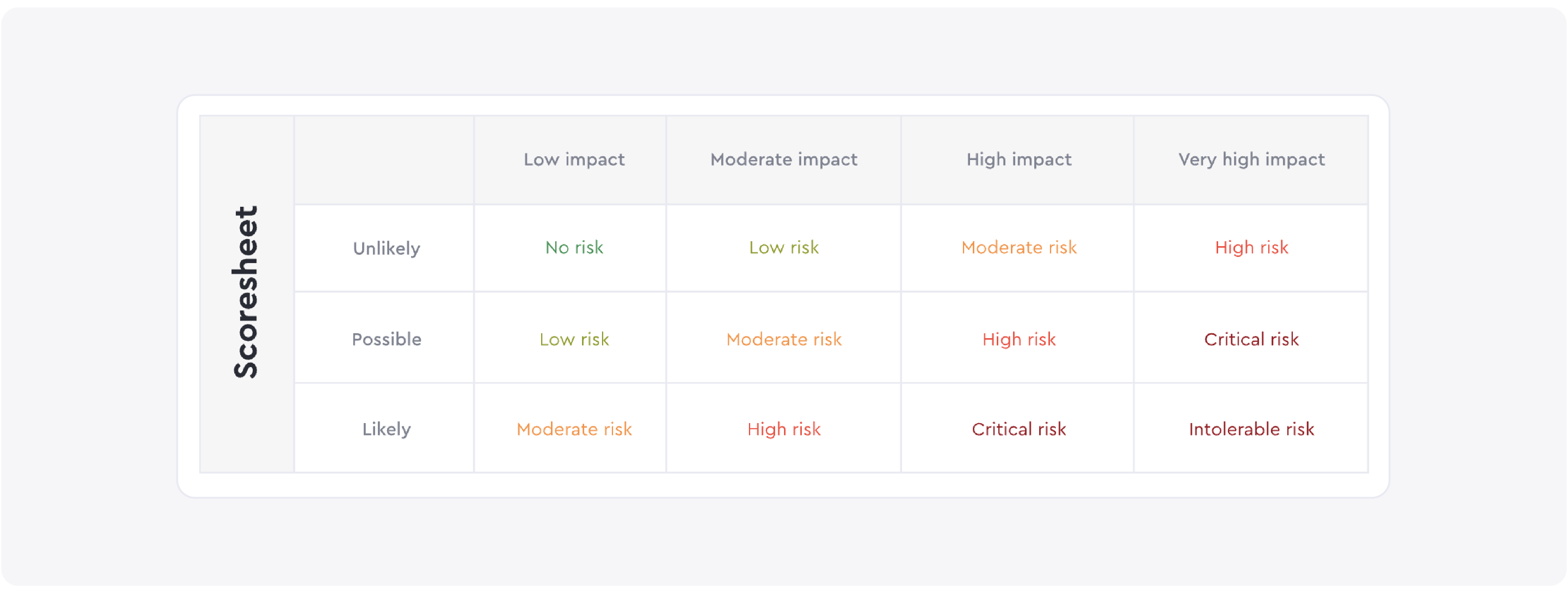
Part 2 - Develop a scoring system
A scoring system is a tool you’ll use to grade your hybrid work security. It’ll categorize workplace security risks by likelihood and severity. If you don’t want to create a custom system, you can use the one below.
Step 3: Do the security assessment
Now that you’ve identified threats for each pillar and created a scoring system, you can complete the security assessment matrix. Below is an example of how a completed matrix might look. Read our guide for step-by-step instructions on how to conduct the assessment.
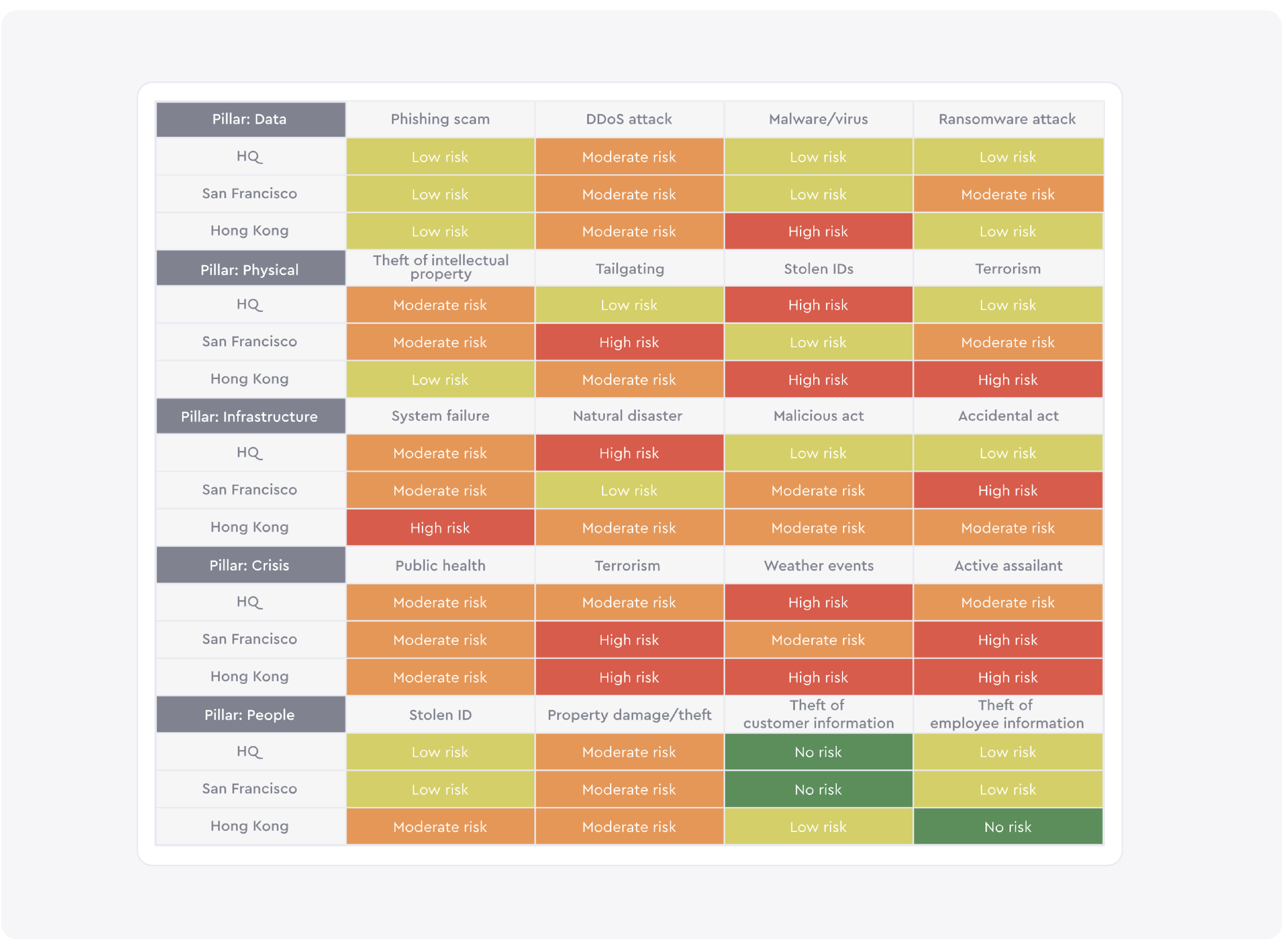
Understanding the results
Once you’ve filled out the matrix, the results of the assessment should show:
- The strengths and weaknesses of your security for each hub
- The strengths and weaknesses of each security pillar across all hubs
For example, say Hub 1 scores well for infrastructure security. You can use this hub as a model to scale this pillar’s security programs to other hubs. Poor scores across a single pillar could reveal a systemic issue. For example, you may be missing critical training programs that teach employees how to identify and mitigate cybersecurity threats.
How to prioritize improvements
You won’t be able to address every threat at once, so you should have a plan of action to guide your team’s focus. You might consider listing out the work you need to do in order of priority. For example:
- 1st priority: Intolerable Risks - These are the risks you can’t put off. Failing to address them could put business continuity at stake.
- 2nd priority: High Risks, Critical Risks – These risks are important to address. They may have a serious and lasting impact on your company.
- 3rd priority: Moderate Risks – These risks may impact business operations but they won’t cause lasting damage.
Or you might decide to focus on a particular hub or pillar. If scale is a priority, consider addressing the threats associated with a single hub first. Once the hub scores well across pillars you can scale its security programs to other hubs.
—
Conducting a security assessment is an essential step to securing your company in the era of hybrid work. Using the framework above will help you identify and prioritize critical improvements.
For more guidance, download our new ebook, An executive framework for scaling hybrid work security. In it, we break down every step of the assessment process, including how you should approach scaling changes to your security programs.
Read more
Workplace security is critical to the future of your business. Learn why it matters, what threats to watch for, and how to strengthen your workplace security plan.
Searching for a visitor management solution? Learn what to look out for and how to choose the best tech for your team.
Managing your space well doesn’t have to be difficult. But if you want to be successful, you need the right approach.
A well-run workplace can set your team up for success. Learn why workplace management matters and how to do it right.
With more folks sending personal packages to the workplace, having a sound mailroom management system in place is key.









