SIMPLIFY TRADE COMPLIANCE
Visitor compliance checks, done the moment they walk in.
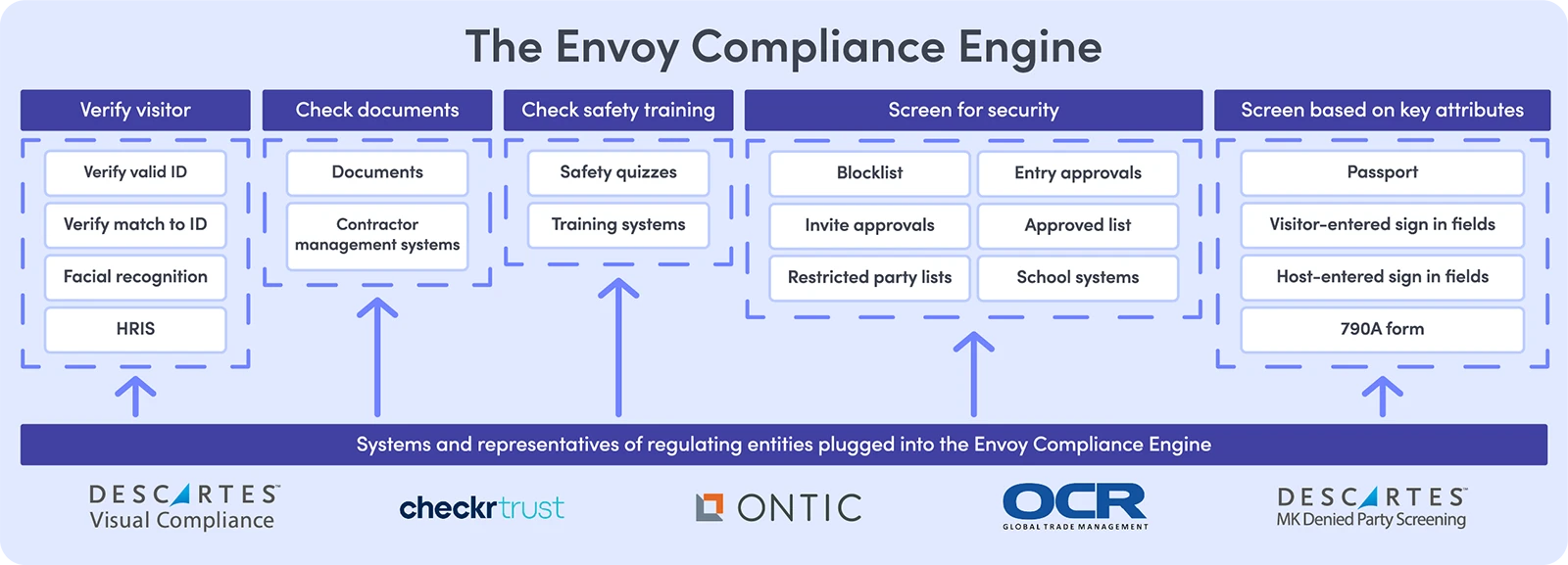
Envoy automates ID verification, document capture, training validation, and security screenings—so you stay audit-ready without adding lobby friction.

Verify IDs in seconds
Instantly scan government ID, match the live photo to the card image, and cross-check HRIS records—no extra wait.

Screen against every watch list
Automatically compare each visitor to internal blocks, restricted-party databases, and government watch lists before a badge prints.
Automate profile-based workflows
Citizenship, visit purpose, or contract codes can launch extra documents, safety quizzes, or manager approvals—ensuring the right control set every time.
Customize access levels based on risk
Provision custom access levels, and issue visitor badges that display escort status, photo ID, and expiration time.

Simplify audits by capturing record automatically
Signed NDAs, entry points, and visitor details log instantly—removing manual tracking and capturing the right data every time.
Track access in real time
Live dashboards show who’s on-site, where they are, and how long they’ve been there, giving security instant situational awareness.
Monitor compliance centrally
Unified logs archive every visit across all locations, making it easy to spot gaps, enforce policies, and prep for inspections.
Export audit-ready reports
Generate time-stamped PDFs or CSVs in seconds—with signatures and access logs included—to satisfy auditors and customers alike.
Standardize compliance workflows
Apply the same visitor protocols at every site with global templates and rule sets—no gaps, no improvising.

Automate compliance at scale
Global sign-in templates handle core requirements everywhere, while local teams add site-specific steps only when needed.
Protect sensitive data
Granular permissions lock down compliance records so only authorized staff and auditors can view or edit them.
Onboard teams faster
Standard templates and dashboards let new security or front-desk staff get fully up to speed in minutes, wherever they work.

Jonathan Priganc
Director, Business Systems–Corporate Affairs
Powered by authoritative compliance sources
Envoy syncs directly with government databases and accredited watch-list providers, so every check reflects the same data regulators rely on.
Competitive landscape
Proactively ensure compliance with visitor automated ID verifications, digital document capture, training validation, and security screenings before arrival.
















































































Explore more resources to improve your building management
In this blog post, we cover the basics of compliance management, including what it is, common compliance standards, key elements, and more!
Let’s break down everything you need to know about ITAR, including what it is, who needs to comply, and who’s exempt.
Join us for a deep dive into the differences between ITAR and EAR—and what they mean for your compliance strategy.





